Cyber Security Awareness Part 5: Internet And Physical Security
- Product ID
- sonicsai_vod
- Training Time ?
- 15 to 19 minutes
- Language(s)
- English
- Video Format
- High Definition
- Required Plugins
- None
- Number of Lessons
- 4
- Quiz Questions
- 4
- Closed Captioning
- Question Feedback
- Wrong Answer Remediation
- Lesson Bookmarking
- Downloadable Resources
The fifth and final part of this series on cyber security awareness, continues to explore digital risks via an interview with a black hat hacker. These risks may come from benign activities such as using the Wi-Fi hotspot at your local coffeeshop or hotel. Even the simple task of browsing the internet may place you in danger. This part of the series explains these hazards and provides tips to protect yourself when you need to use the internet in public.
A typical public network is unencrypted, which means hackers may be able to access your data. Hackers can even make their computers look like a familiar hotspot so your computer connects to it. The hacker can then extract user names and passwords, and even record Skype calls. The first line of defense to this kind of attack is to identify whether a network is public or secured. Then, you should recognize which websites are secure, as well as when you should use them. After all, browsers are often the first targets for malware programs and cyber criminals. This course explains these practices, including what makes a website secure.
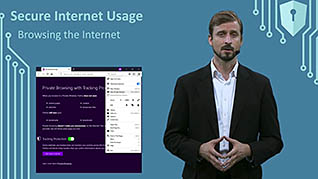
This lesson demonstrates the steps you can take when browsing the internet to decrease the risk of becoming the victim of a cyber-attack. For example, you can make your browser session private. You can also use a VPN (Virtual Private Network), which you will learn about here, as well as physical devices such as screen blockers.
We all use the internet on a daily basis. Therefore, it is important to know how to best protect ourselves and our personal information. Utilize the material provided in this training video and make yourself, and your data, more secure.
![]() This course is in the Video On Demand format, to read about Video On Demand features click here.
This course is in the Video On Demand format, to read about Video On Demand features click here.

- Install on any SCORM LMS
- Full-screen video presentation
- Print certificate and wallet card
- You have 30 days to complete the course
All employees
- Using Wireless Devices
- Browsing The Internet
- Maintain Physical Security
- Moving Forward
© Mastery Technologies, Inc.